AWS Systems Manager (SSM) is a service that helps manage and automate tasks on systems running in AWS. It allows you to execute commands, manage configurations, and securely access instances without needing SSH. At the core of SSM is the SSM Agent, a small program that runs on your system and communicates with the AWS Systems Manager service.
SSM provides tools like Session Manager for remote shell access, Run Command for running scripts or commands, and Parameter Store for managing configuration values and secrets. These features simplify system management and improve security by avoiding direct network exposure.
In this blog post, I will show how to set up AWS SSM with OpenBSD using awscli and the AWS web console, enabling remote management while staying aligned with OpenBSD’s focus on security and simplicity. While SSM eliminates the need for SSH, I consider this a security trade-off, as there is no protocol or software I find more secure than SSH. Unfortunately, this compromise must be accepted when using SSM.
Setup the OpenBSD box. #
Simply install and enable the amazon-ssm-agent package by pkg_add(1).
$ doas pkg_add amazon-ssm-agent
$ doas rcctl enableamazon_ssm_agent
Setup SSM by awscli #
Install awscli and configure your AWS Access Key ID and security credentials:
$ doas pkg_add awscli
$ aws configure
# ... flow inscructions
First of all we need an IAM role with the required policy AmazonSSMManagedInstanceCore.
Our role is names AmazonSSMManagedOnPremInstanceRole
$ aws iam create-role \
--role-name "AmazonSSMManagedOnPremInstanceRole" \
--assume-role-policy-document '{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ssm.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}'
# Attach the Required Policy
$ aws iam attach-role-policy \
--role-name "AmazonSSMManagedOnPremInstanceRole" \
--policy-arn "arn:aws:iam::aws:policy/service-role/AmazonSSMManagedInstanceCore"
We can easily create a “Hybrid Activations” named openbsd.org via the cli.
When creating a Hybrid Activation, specify this role using the –iam-role
parameter:
$ aws ssm create-activation \
--default-instance-name "openbsd.org" \
--description "Hybrid Activation for On-Premises Servers" \
--iam-role "service-role/AmazonSSMManagedOnPremInstanceRole" \
--registration-limit 10
# --expiration-date "pics/2025-01-23T23:23:59Z"
If the command is successful, an output similar to this is returned:
{
"ActivationId": “abc12345-6def-7890-gh12-ijk345lmnwww",
"ActivationCode": "3abcd12efg34h567ijklmno"
}
ActivationId and ActivationCode are required to register the OpenBSD system in the next task.
Register the OpenBSD system #
export ActivationId=“abc12345-6def-7890-gh12-ijk345lmnwww"
export ActivationCode="3abcd12efg34h567ijklmno"
$ doas amazon-ssm-agent -register -code "$ActivationCode" -id "$ActivationId" -region "eu-central-1"
Initializing new seelog logger
New Seelog Logger Creation Complete
pics/2025/01/23 11:20:35 Found config file at /etc/amazon/ssm/amazon-ssm-agent.json.
Applying config override from /etc/amazon/ssm/amazon-ssm-agent.json.
pics/2025/01/23 11:20:35 processing appconfig overrides
Found config file at /etc/amazon/ssm/amazon-ssm-agent.json.
Applying config override from /etc/amazon/ssm/amazon-ssm-agent.json.
processing appconfig overrides
pics/2025-01-23 11:20:35.7809 INFO Successfully registered the instance with AWS SSM using Managed instance-id: mi-00fbca0b0XXXXXX
If everything is successful, we can start the service and look at the logs:
$ doas rcctl start amazon_ssm_agent
amazon_ssm_agent(ok)
$ tail -f /var/log/amazon/ssm/amazon-ssm-agent.log
You can check out your registered instance in the AWS Console or via awscli:
$ aws ssm describe-instance-information
{
"InstanceInformationList": [
{
"InstanceId": "mi-00fbca0b0XXXXXX",
"PingStatus": "Online",
"LastPingDateTime": 1737632479.387,
"AgentVersion": "3.3.0.0",
"IsLatestVersion": false,
"PlatformType": "Linux",
"PlatformName": "OpenBSD",
"PlatformVersion": "7.6",
"ActivationId": "abc12345-6def-7890-gh12-ijk345lmnwww",
"IamRole": "service-role/AmazonEC2RunCommandRoleForManagedInstances",
"RegistrationDate": 1737627635.743,
"ResourceType": "ManagedInstance",
"IPAddress": "152.XX.XXX.XXX",
"ComputerName": "test.sizeofvoid.org",
"AssociationStatus": "Success",
"LastAssociationExecutionDate": 1737631317.532,
"LastSuccessfulAssociationExecutionDate": 1737631317.532,
"AssociationOverview": {
"InstanceAssociationStatusAggregatedCount": {
"Success": 1
}
},
"SourceId": "mi-00fbca0b0XXXXXX",
"SourceType": "AWS::SSM::ManagedInstance"
}
]
}
Setup SSM by AWS web console #
-
Open the AWS web console in your favorit web browser and select your preferred region. Keep in my your IAM user needs the
AmazonSSMFullAccesspolicy rights. Then navigate to AWS Systems Manager main window and select Hybrid Activations under Node Tools. You can find it on the left side
AWS Systems Manager main window 2025/01 -
Select Create activation and fill out the inputs:
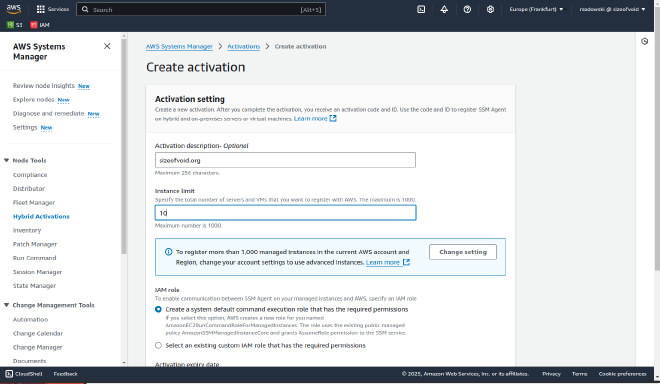
AWS Systems Manager - Create activation -
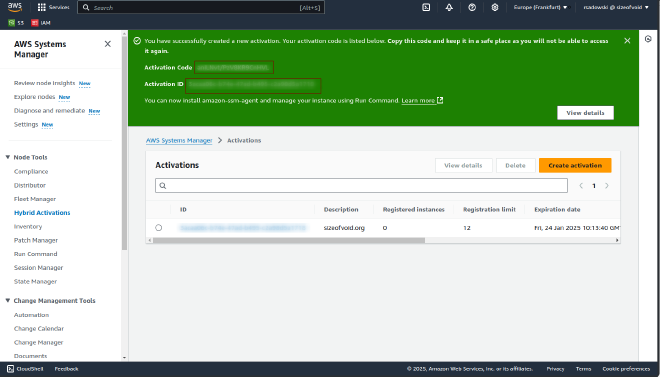
Once everything necessary has been filled in and you have clicked on create, it is important to observe the information in the green bar.
Save the ActivationCode and use it in the ssm register process…
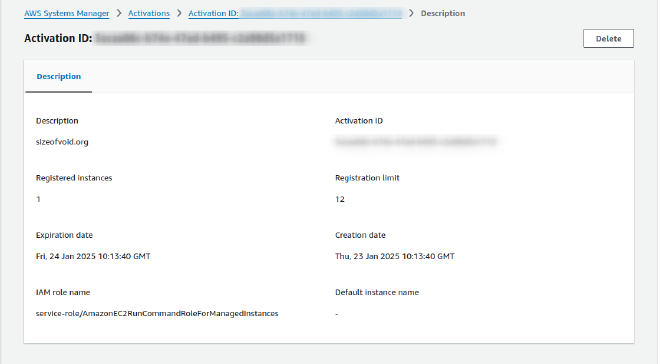
Finally you can see your registered instance in Fleet Manager
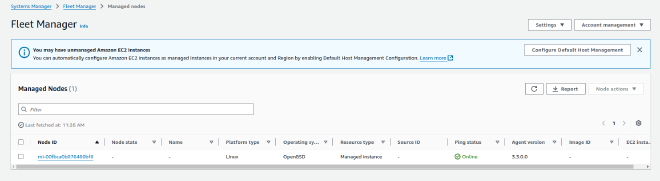
Once we have installed the SSM agent on our OpenBSD instance, we can now easily monitor it with SSM. This allows us to update the system, run automated tasks and more. I’ll be adding useful use-cases in future blog posts.
